Software Security
Gain security insights, take action faster and modernize your architecture with Datawalls, we defend against cyberattacks with proactive, focused, industry-relevant threat intelligence to give you the confidence that comes from knowing your business is secure. Anytime. Anywhere.
Vulnerability Assessment
We assess your technological maturity and readiness for AI-driven automation and follow you through all the stages of adopting artificial intelligence in your business operations, from analyzing your use case to developing AI-driven software and ensuring its positive user buy-in.
Security Audit
We assess your technological maturity and readiness for AI-driven automation and follow you through all the stages of adopting artificial intelligence in your business operations, from analyzing your use case to developing AI-driven software and ensuring its positive user buy-in.
Penetration Testing
We assess your technological maturity and readiness for AI-driven automation and follow you through all the stages of adopting artificial intelligence in your business operations, from analyzing your use case to developing AI-driven software and ensuring its positive user buy-in.
Compliance Testing
We assess your technological maturity and readiness for AI-driven automation and follow you through all the stages of adopting artificial intelligence in your business operations, from analyzing your use case to developing AI-driven software and ensuring its positive user buy-in.
Security Code Review
We assess your technological maturity and readiness for AI-driven automation and follow you through all the stages of adopting artificial intelligence in your business operations, from analyzing your use case to developing AI-driven software and ensuring its positive user buy-in.
Security Stress Testing
We assess your technological maturity and readiness for AI-driven automation and follow you through all the stages of adopting artificial intelligence in your business operations, from analyzing your use case to developing AI-driven software and ensuring its positive user buy-in.
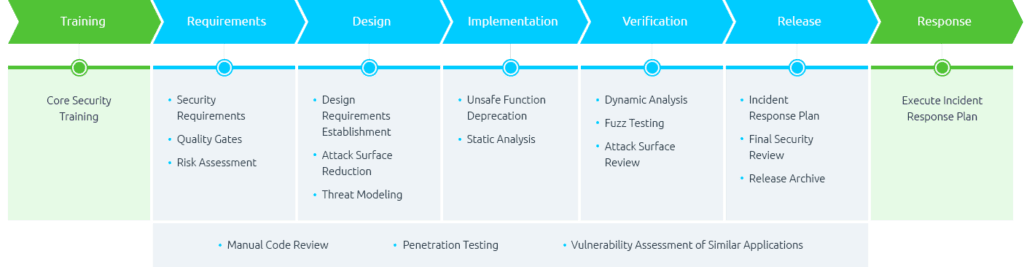
We put security everywhere
We Protect your business with a security strategy defined by zero trust. We build security pillars at all levels, helping organizations minimize the risk of security incidents throughout the SDLC and release cyber-immune solutions.
Test Your Users and Your Network
We Protect your business with a security strategy defined by zero trust. We build security pillars at all levels, helping organizations minimize the risk of security incidents throughout the SDLC and release cyber-immune solutions.
Dynamic application security testing (DAST)
While applying this black-box testing technique, our certified ethical hackers try to compromise a running web app from the outside. By simulating the most popular cyber attacks, we check how reliable and ready a web app is to hold out against a real intrusion.
Static application security testing (SAST)
We perform SAST concurrently with app development to verify the solution contains no flaws and can be deployed securely. This white-box testing method helps release healthy and protected web apps along with reducing the investment into post-deployment testing.
Client-side app security testing
Trying to execute attacks on the client-side of a web app, we reveal how susceptible the app is to commonplace attacks, including XSS, HTML injections, CORS, clickjacking, etc. We assess the severity of detected vulnerabilities and their potential impact in case of a successful penetration.
Server-side app security testing
Our services cover embedded firmware analysis and testing. We work to prevent security flaws in stand-alone and connected devices to guarantee their operational and data safety.
